Cloud Computing, Types of Cloud Computing, Architecture of Cloud Computing & Services of Cloud Computing.
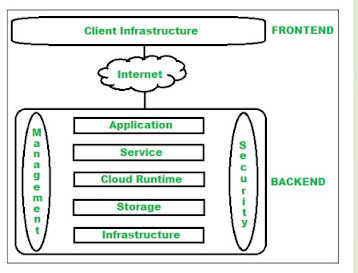
Cloud Computing Cloud computing is the on-demand delivery of IT resources over the Internet with pay-as-you-go pricing. Instead of buying, owning, and maintaining physical data centers and servers, you can access technology services, such as computing power, storage, and databases, on an as needed basis from a cloud provider like Amazon Web Services (AWS), Google Cloud Platform. The following are some of the Operations that can be performed with Cloud Computing Storage, backup, and recovery of data Delivery of software on demand Development of new applications and services Hosting blogs and websites Analysis of data Streaming videos and audios Benefits of cloud computing Cost-cutting: Reduced infrastructure costs and pay-as-you-go pricing models. Scalability: Easily scale resources up or down based on demand. Flexibility: Access services and data from anywhere with an internet connection. Reliability: Facilitates data backup, disaster recovery, and business continuity at multiple ...
.png)

.png)


.gif)
