What do you mean by Elastic IP Addressing? Describe how Elastic IPs works in cloud service.
Elastic IP address An Elastic IP address is a static IPv4 address designed for dynamic cloud computing. An Elastic IP address is associated with your AWS account. With an Elastic IP address, you can mask the failure of an instance or software by rapidly remapping the address to another instance in your account. An Elastic IP address is a public IPv4 address, which is reachable from the Internet. If your instance does not have a public IPv4 address, you can associate an Elastic IP address with your instance to enable communication with the Internet; for example, to connect to your instance from your local computer. Elastic IP addresses are used by AWS to manage its dynamic cloud computing services. Within the AWS infrastructure, customers have virtual private clouds (VPCs). Within the VPCs, users have instances. The Elastic IP address is what is used to advertise the data within the instance to the public internet. Works: Each EIP can be assigned to one instance, in whi...
.png)
.png)
.png)
.png)
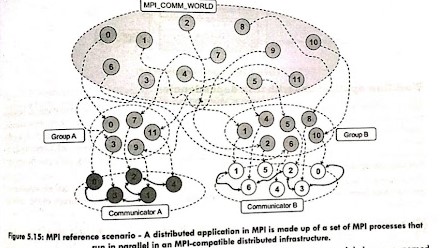

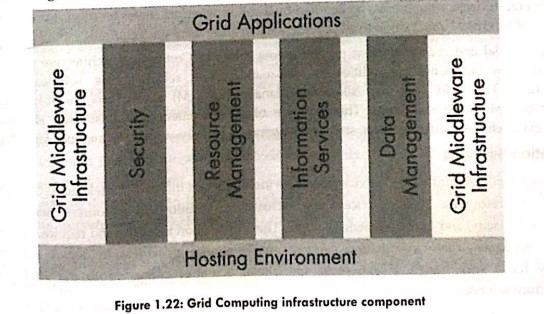





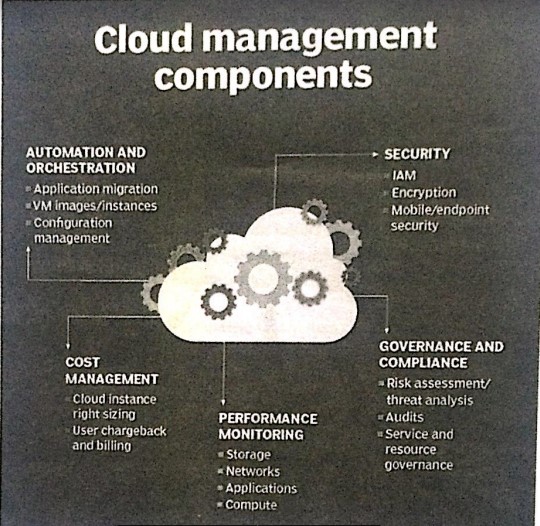
%20do%20this!%20(1).png)